
"It is
impossible for ideas to compete in the marketplace if no forum for
their presentation is provided or available." � �Thomas Mann, 1896
TruPrevent Technologies: Technical Overview
Sponsored by Panda Software (USA), Inc.
The need for protection technologies against unknown malware:
Current antivirus technologies are extremely effective for detecting and disinfecting known malware (any that is found in their databases of signatures), however, from the moment that a new malicious code appears until the antivirus solutions are capable of detecting it and disinfecting it, the following events must arise:
-
A new malicious code appears
-
It starts to spread
-
The manufacturer of the antivirus obtains a sample It is analyzed in its laboratory
-
The manufacturer creates a identifier for the new malware
-
The update is prepared and it is uploaded onto Internet
-
The clients update according to the conditions established
Result: from the moment that a new malware appears until the users are protected anything from a few hours up to several days may pass by, depending on the haste with which the manufacturer producing the antivirus reacts before the appearance of the new threat.
During that reaction time, the users of the antivirus product are left without support from that technology to prevent the infection.
The weapons that the user had till now to face up to this situation were:
-
Heuristics technologies for antivirus: The current generation allows unknown malware to be detected, but they are prone to false positives. If their level of sensitivity drops, they detect few unknown malware.
-
Corporate firewalls: they act on a network level and provide a filter for the communications that cross through corporate networks in both directions, defining a security policy that may be useful against some basic types of attack but which turn out to be completely ineffective against other types of attack on an application level, for example.
-
Distributed firewalls: They are components that define the network access policies for each one of the machines within the corporate network, for both workstations and servers. They allow different policies to be defined for each group of users by granting access to certain services for the groups of users that require it. These are useful with a view to detecting certain types of attacks but do not mean full protection.
-
Intrusion detection systems (IDS): they detect anomalies in traffic and alert the administrator, with the latter being the one who has to act against the malware (generally by altering the configuration of its corporate firewalls) hence they mean that human resources are dedicated to security permanently.
-
Intrusion prevention systems (IPS): The IPS, unlike the IDS, block the attacks. Both those based on signatures and those based on detection by anomalies although they detect and block certain network attacks. However their greatest problem is the abundance of false positives that they generate. They are also aimed at attacks arriving from outside of the network, when it is true now that the attacks started from within are ever more frequent even though it may be in an involuntary way (for example, when connecting an infected laptop to the company’s Intranet).
-
Host intrusion prevention systems (HIPS): They intercept the actions of the applications that function on a host. Most are based on the detection of anomalous behaviors by means of rules, hence the rules have to be specific for the type of host protected (otherwise they produce false alarms, or they have a very low detection rate). If the rules are too generic (not adapted to the type of host) it requires the intervention of the user or administrator to decide on each breach of a rule.
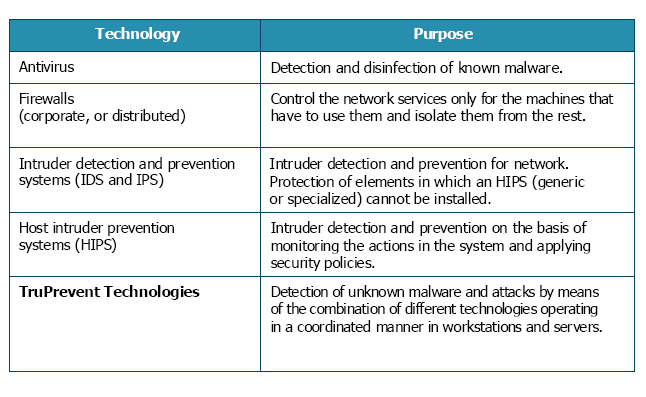
Where does TruPrevent Technologies fit in?
TruPrevent Technologies is a set of technologies aimed at enhancing the security of the systems against attacks from unknown malware. Its purpose is protecting the user against malware that have just appeared and that traditional security products are incapable of combating because they are unknown for them. TruPrevent Technologies is a combination of technologies of different kinds with a common purpose: protecting workstations and servers against unknown threats, hence it is hard to label it within a single category within security solutions.
The technologies that make up TruPrevent Technologies interact between each other so that the degree of protection that is achieved is greater than that of any other solution. They are specifically designed for avoiding false positives and for taking decisions without any need for the end users or the administrators to intervene. These two points affect both the ease of use and administration, and the security of the system:
-
By avoiding false positives, we avoid causing interferences in the work for the users of the network with the applications and we also prevent their loss of trust in the system.
-
By avoiding decision-making by users or administrators, we minimize the risk of infection due to attacks in which social engineering is used (there have also been cases of malware that have used social engineering against administrators). The end user is quite often a user without any technical knowledge and he cannot be given the responsibility to decide about blocking a process or not after detecting some suspicious activity. TruPrevent Technologies are capable of clearly discerning whether we are faced with malware that has just appeared or not, and if so, it will take the necessary actions for ensuring the security of the system protected and so for the whole network to which it belongs.
TruPrevent Technologies
complement the rest of the existing security technologies (Antivirus,
Firewall, IDS/IPS, HIPS ). It specializes in detecting and avoiding the
harmful effects of unknown malware, and as such, it is the ideal
complement for the technologies specializing in the detection and
disinfection of known malware.
A system of perfectly coordinated modules:
TruPrevent Technologies are based on the combination of different technologies for detecting unknown malware, amongst which the following stand out:
-
A security policies management module
-
A Buffer Overflow detection module, which detects buffer overflows in the stack and the heap of the processes.
-
A network virus detection module that analyzes the data packages in search of signatures of known virus.
-
An unknown malware detection module using event correlation techniques.
The technologies included in TruPrevent Technologies perform a coordinated task for analyzing the processes in execution, so each one of the operations that they perform is controlled.
Let’s imagine that an application requests a service from the operating system during its execution:
-
The application wants to execute an action that affects a resource from the operating system, of the type “write or access a file in the hard disk”, “modify the Windows log”, “open a communications port” or “send/receive data using the network card”.
-
The security policies management module checks that the operation is allowed or not for this application. Depending on that result, TruPrevent Technologies will block or not the execution of the action at this point.
-
If this application also has any interaction with the network, because it is listening at a port for example, the packages exchanged across the network are analyzed so as to discard possible attacks of the network virus type.
-
If the instruction is not rejected by any of the preceding modules, this one is executed in the operating system, and the buffer overflow module is in control at all times so that the instruction will not create a buffer overflow. If this should occur, it would immediately block the execution of the process affected.
-
The correlation of events detection module, in parallel, takes into account the whole “history” of the activity of the application so as to determine whether it involves a malicious process or not.
Now consider how each one of these modules functions in detail:
Detecting and blocking attacks and unknown malware using application security policies The security policies are security solutions aimed at specific working environments. They are made up by containers of rules, each one of which is the solution to a given security problem. The rules that make up these containers determine that the action or actions may or may not be performed on a given group of resources from the system by an application or a group of applications in the security environment for a given user’s profile.
The security policies are made up by a set of rules that control the access of the applications to the resources in the system. So secure behaviors are established for the applications, so that any malware introduced into the system or an attacker will see how the harmful actions that they mean to perform on the system are blocked. Specifically speaking, there are different types of rules:
-
Access to archives: these rules are used for allowing or refusing the operations (creation, reading, execution, modification) that certain applications and users can perform on certain archives and directories.
-
Access to a log for the system: these rules are used for allowing or refusing certain applications to modify or create given entries in the Windows log.
-
Access to user accounts: These rules are used for allowing or denying, for certain applications and users, certain operations (modify, create) with the user accounts. These operations are usually related to scales of privileges after successfully exploiting vulnerabilities in privileged applications.
-
Access to network resources: These rules are used for controlling the access of the unit to the network and of remote units to the services offered by the local applications.
-
Access to COM components: These rules are used for allowing or denying certain applications access to certain COM components.
-
Access to Windows services: These rules are used for allowing or denying certain operations for certain applications and users, (start up, modify, create) with the Windows Services.
Managed Security:
The security policies are modified and updated from Panda (managed security) including solutions for security problems that may have been detected in the most common software products. So a solution can rapidly be taken against a vulnerability discovered in a software component prior to the publication of the patch by the manufacturer.
These predefined policies that are updated from Panda are sufficient for the protection to work effectively, providing a high degree of security for the systems protected and making the concept of managed security effective: it is Panda that takes charge of defining and updating, on the basis of the trends of action for the malware, these security policies without the intervention of security experts being required at the client’s premises.
These policies have been defined at Panda following an exhaustive study of the actions performed by the malware for damaging systems and controlling the access to the basic resources of the system such as the log for inputs, COM components, files, network, users’ accounts and services of the system, restricting their access to legal applications and so preventing third parties or third party software can damage the system.
The policies are established on the basis of the different environments protected in a modular way, so that some given policies are established for Windows systems, for workstations and for servers, as well as distinguishing within server environments by means of their function within the corporate network (Web servers, database servers, mail servers). The function of each one of these elements within the corporate network is very different and therefore the need for access to resources of the software that is executed in each one of them is specified for each element.
Some examples of these rules are:
-
Office computer applications cannot gain access for writing in any executable.
-
The main mail clients, Web browsers and instant message applications must not be able to write in critical directories of Windows, such as the installation directory for Windows or the system directories, SYSTEM and SYSTEM32
-
The e-mail clients can only access the network services used for e-mail.
These rules are defined bearing in mind what the needs are for accessing resources from the system for the common software however specific the latter may be, so that it does not limit its operation or interfere in its functioning, since not generating false alarms is the basic premise on which the new TruPrevent Technologies have been designed. So any action that may be deemed to be dangerous or harmful will be blocked so preventing the malware unknown or an attacker from being able to damage the system.
When a process attempts to violate any of the rules, a security policy may be added dynamically to a group of processes for which a certain, more restrictive security policy may be applied, with the result that there will be a correlation of events for the actions performed by the process in the system.
Security policies for the administrator:
The security policies management module offers the administrator the possibility to add new security policies specifically designed by him. The administrator will have all the tools needed to clearly and simply generate the containers and rules of different types that he may deem to be necessary. Specifically speaking, he may define the same types of rules as those that are produced by Panda.
So the administrator will be able to modify the behavior of the policies defined by Panda by adding more priority policies.
Detection of Buffer Overflows:
Buffer overflows are caused by exploits, or attacks that take advantage of the vulnerabilities in the software installed on the computer under attack, related to the fixed memory space reserved by applications to store incoming data.
Two concepts are more thoroughly scanned.
Vulnerabilities and exploits:
A computer vulnerability is an error in a software component that may mean a threat for the security and integrity of the system. There are different types of vulnerabilities, but the buffer overflow ones are by far the most widespread ones. These kinds of vulnerabilities are discovered in all kinds of software practically every day.
An application is vulnerable to a buffer overflow attack when it reserves a fixed space in memory for storing a data input and does not check the real length of that data prior to its insertion in the space reserved. These kinds of programming errors arise in all kinds of applications, affecting both workstation environments and server environments.
When the manufacturer of the vulnerable software solves the problem that causes security gap, it publishes a patch, that must be applied to the vulnerable software. During this time window between the discovery of the vulnerability and the publication of the security patch, the system is vulnerable to attacks.
An exploit is an attack on a computer system that takes advantage of a vulnerability that a software component offers for an intruder. Should the exploits that take advantage of buffer overflow vulnerabilities arise, it leads to the sending of a specific data string with an excessive length and not envisaged in memory buffer for a given process.
The problem arises when the process does not check the length of this string and writes its whole contents in the memory. This string with a length greater than that envisaged overwrites the original contents in memory and so the return address, so if an attacker specifically designs that string he can redirect the execution to an area in which he himself has put executable code and therefore achieve the execution of his own code in the system attacked. Therefore the attacker can take control of the system attacked.
The easiest type buffer overflow to exploit (though not the only one) is the buffer overflow in the stack. The variables utilized by a function of a process are stored within the area of memory assigned to the stack, and finally the return address to which the execution of a process will be redirected once the execution of the function has ended. In this type of attack, once the amount of data the overflow may produce is known, an attacker uses an input string, which is really an executable code and modifies the return address precisely in order to cause the redirecting of the execution of the application towards his own code. The string overwrites the return address that had been stored beforehand in the stack over the code that he wants to execute as shown in the figures.
When the execution of the function that had reserved the buffer is over, the operating system will take the return address that it has stored in the stack, but the latter is now altered by the code entered by the attacker. Hence, the attacker can execute the code that he wants. Very often the code that he has been able to insert in the process attacked is a small amount, and only manages, for example, to execute a function for downloading the code that he wants to execute from a server.
On other occasions, all the code that he wants to execute may be entered this way.
Patches for vulnerabilities and vulnerability window:
The time that elapses from when a vulnerability is discovered and the manufacturer of the application distributes a correction in the form of a patch represents a vulnerability window. Sometimes, the manufacturers of software correct the vulnerabilities before the latter can be exploited, and in this case a proper policy for updates in our applications may keep us protected. The problem is greater the more this vulnerability window grows, since it gives the attackers longer to develop exploits that will take advantage of these vulnerabilities, and the installations will remain unprotected for longer.
The current trend for creators of malware is to develop exploits in an ever faster way as from the appearance of a given vulnerability so no time for reaction is given to the software manufacturers for publishing patches. An added problem is that the appearance of an ever greater number of vulnerabilities often means that it is complicated to keep the large amounts computer equipment updated as far as the application of patches is concerned.
How TruPrevent Technologies acts:
The buffer overflow detection module included in TruPrevent Technologies monitor the execution of the processes of the system, looking after the areas of data for the processes in execution, controlling at all times that buffer overflows do not arise. Should an overflow arise, TruPrevent Technologies prevent the execution of the malicious code and terminates the execution of the process affected and therefore maintains the integrity for the system. Therefore, we shall be protected against these types of attacks even though they are unknown and our software is not properly patched. TruPrevent Technologies protect us even against the “attacks on day zero” (attacks that arise before the vulnerability itself has been discovered), since it does not need to know the nature of the attack or the vulnerability that it attacks when generically detecting these types of overflow buffer attacks.
TruPrevent Technologies is also capable of generating a signature or identifier for this attack that has taken place against a vulnerable software component and send it on to the network virus detection module so that subsequent attacks of the same kind will be repelled on a level of the filtering of packages in the Firewall and will not even manage to penetrate the vulnerable unit.
Detection of network virus:
The network virus constitute a type of attack that does not reach the machine in the form of a file like a ‘traditional’ virus but rather that the attack arises through the sending of packages directly to a port in which it is listening to the process attacked. This requires special treatment for its detection since what has to be done is to locate certain packages within the IP connection and not a file as in the usual case for a virus or a worm that reaches it or any other mechanism.
The network virus come from another machine in the network (whether it be a private network or Internet itself) and attack the vulnerable machine without any need for the user to do anything at all, which makes them even more dangerous.
Network virus are attacks that are aimed at exploiting vulnerabilities in certain services for processes that are running in the machine attacked A pure network virus does not write on the disk but rather it injects code in the process that it attacks and so it is capable of performing its malicious activity.
Because they do not write on the disk, they cannot be detected by traditional antivirus. However some combined attacks may even write on the disk looking for a mechanism to become resident in the machine and be able to execute themselves in new restarts, so converting the machine attacked into a new focus for generating attacks on other machines. This trace that they leave on the disk can be detected by traditional antivirus but its disinfection does not prevent the unit from being attacked by means of the injection of code in the process attacked.
How network virus detection works:
The system detector of network virus is based on the analysis of the contents of the packages that cross through the network interface for the machine protected. By means of the utilization of Firewall technology an analysis of the fields in the IP link is carried out to look for signatures of known attacks.
This system functions on the basis of two types of signatures:
-
Signatures of known attacks: The system comes preconfigured with signatures that allow it to detect the attacks by network virus that are already known.
-
Signatures of attacks generated by the system itself: these signatures correspond to attacks that the buffer overflow detection module has detected and has subsequently generated a signature of the attack automatically to prevent it from penetrating into the system in successive repetitions of the attack. They are attacks that are still unknown for the manufacturers of security solutions but against which the system is already capable of reacting.
Detection of unknown malware using behavior analysis:
This component, analyzes the behavior of each and every one of the processes that are executed in the workstations and servers on the network. It is not a simple analysis based on single rules that prohibit or allow certain actions: it is an analysis that takes into account the set of actions performed by any process from the time at which it appears for the first time in the operating system (correlation of events). The advantage of this method lies in the fact that the system acts immediately as soon as it has gathered enough evidence that a process is malicious: it is specifically designed to avoid false positives (detection as malware of processes that really are not) and the system functions autonomously, it does not require the end user to have to take decisions, unlike what happens in other products from the competition that merely ask the user whether the malicious actions that they halt can or cannot be performed.
The products that are based on the application of a set of simple rules (allow/deny) on the actions that the processes perform in the system are prone to generating false positives since they do not have enough information about the context of the process in question and its history in the system in order to take the appropriate decision. These kinds of products based on the application of atomic and uncorrelated rules are usually guilty of being highly restrictive (they generate many false positives) or on the contrary they only combat the actions that very clearly and unequivocally show malicious activity (they are hardly capable of detecting malware).
The TruPrevent Technologies analysis is based on considering all the information available from the process, so by assessing its actions in the suitable context it is decided whether the process is malicious or not. It should be taken into account that many legal applications (installers, specific network management applications ...) perform operations that when considered in isolation might be considered as suspicious and however the usual operation of these programs is not affected by the action of TruPrevent Technologies.
TruPrevent Technologies can also act on two levels depending on the seriousness of the evidence gather from a process:
-
Blocking the outputs from the system of a process: TruPrevent Technologies, by default, block all the outputs and communications from the processes that it identifies as malware, so as to avoid their propagation which is especially important in a corporate environment so as to avoid the network collapses that are so usual in the case of an infection.
-
Blocking the execution of a process: when enough evidence is gathered so as to ensure that the process is going to cause serious damage to the system protected the execution of said process will be halted and no future executions will be allowed so as to avoid harmful actions being carried out on the system.
In either case, and once we have the administrator’s approval, the malicious program will be sent automatically or manually to PandaLabs, where an identifier for it will be developed and the Panda antivirus will be updated so that henceforward, the process will go on to form part of the list of known virus and will be stopped immediately as soon as it is intercepted by Panda antivirus.
TruPrevent Technologies have detected, amongst many others, the following virus with every one of their multiple variants: Mydoom, Bagle, NetSky, Gaobot, Sdbot, Passer, Blaster, Bobax, Bugbear, Dumaru, Klez, Sasser, Sober, Zafi, Nachi and so on, up to over 500 different virus in just the first few weeks since it appeared.
Compatibility of an additional layer of protection:
TruPrevent Technologies are compatible with the rest of solutions and technologies used for protecting our network. Besides it provides an additional layer of protection by adding a combination of technologies capable of securing the machine with a degree of effectiveness greater than that achieved by any of the solutions available on the market.
-
With regards to conventional technologies aimed at detecting known malware (reactive ones) it is the ideal complement given its capacity for detecting unknown threats.
-
With regards to technologies aimed at detecting unknown malware (proactive ones) TruPrevent Technologies include a combination of technologies that are superior in the level of protection offered and number to any of the solutions present on the market.
Integration of TruPrevent Technologies with the rest of the security technologies in our network with the rest of the security technologies in our network:
The information contained in this document represents the current view of Panda Software, S.L. on the issues discussed herein as of the date of publication. This document is for informational purposes only. Panda Software, S.L. makes no warranties, express or implied, in this document. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording or otherwise) or for any purpose, without the express written permission of Panda Software , S.L. Panda Software, S.L. may have patents, patent applications, trademarks, copyrights or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Panda Software, S.L. the furnishing of this document does not give you any license to these patents, trademarks, copyrights or other intellectual property.
Visit the Authors Web Site
![]() Click Here
for The Business Forum Library of
White Papers
Click Here
for The Business Forum Library of
White Papers
![]()

 Search Our Site
Search Our Site
Search the ENTIRE Business
Forum site. Search includes the Business
Forum Library, The Business Forum Journal and the Calendar Pages.
Disclaimer
The Business Forum, its Officers, partners, and all other
parties with which it deals, or is associated with, accept
absolutely no responsibility whatsoever, nor any liability,
for what is published on this web site. Please refer to:
Home Calendar The Business Forum Journal Features Concept History
Library Formats Guest Testimonials Client Testimonials Experts Search
News Wire Join Why Sponsor Tell-A-Friend Contact The Business Forum
The Business Forum
Beverly Hills, California United States of AmericaEmail: [email protected]
Graphics by DawsonDesign
Webmaster: bruceclay.com
� Copyright The Business Forum Institute 1982 - 2009 All rights reserved.